EZ VPN Inc. Launches the First Cloud Remote Access VPN Service
EZ VPN | October 22, 2020
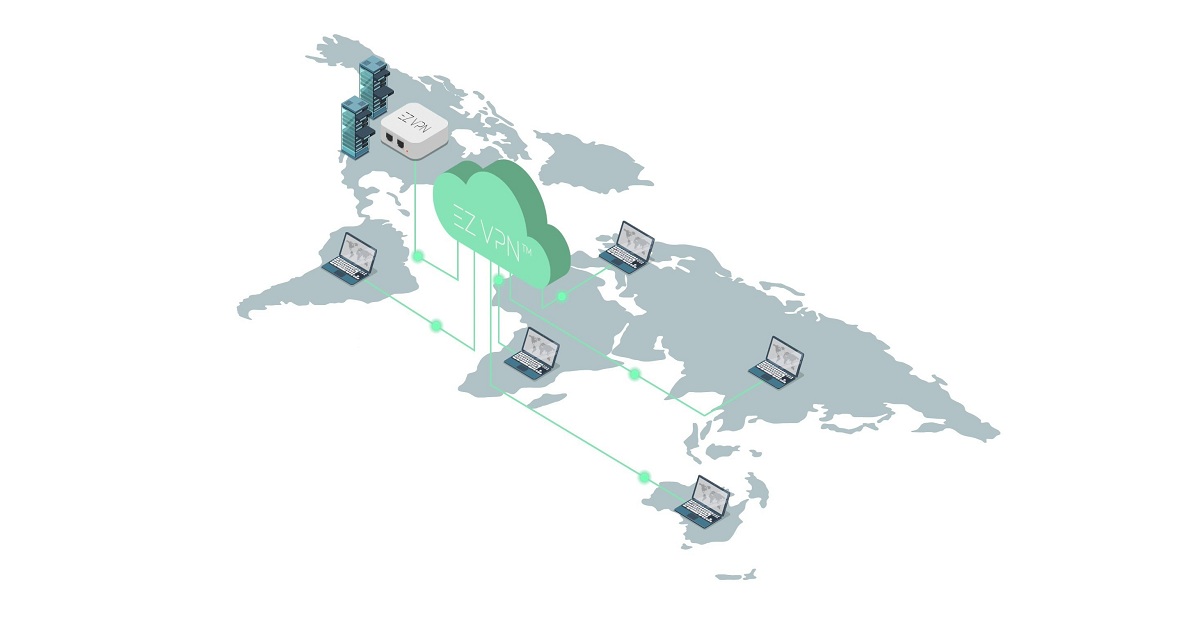
As we begin to shift towards a growing remote workforce, there is much to consider regarding the accessibility of corporate network devices from home. Following such demands would require a Virtual Private Network - a network that permits access to data, resources, and information through a remote site. As this often would require IT personnel to configure, the results are costly and complicated for companies to pursue. Establishing a connection that is both simple and secure is the solution that businesses are in desperate need of. Fortunately, a solution has been developed from those at EZ VPN Inc. who recently launched the first cloud remote access VPN service.