Viavi Introduces a Suite of Products to Support Delivery of VPN Services throughout the Lifecycle
VIAVI Solutions | September 09, 2020
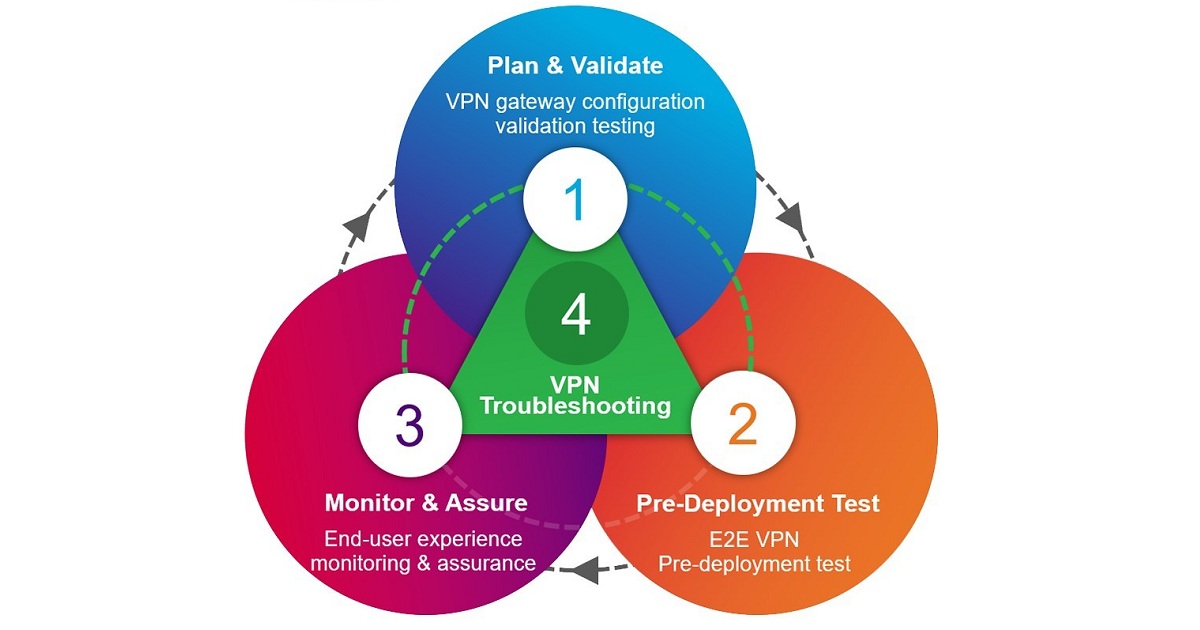
In response to enterprises around the globe adopting remote work as the new normal, Viavi Solutions Inc. has introduced a suite of products to support delivery of VPN services throughout the lifecycle, from validation, to pre-deployment testing, to monitoring, assurance and troubleshooting. According to the Neustar International Security Council, 64% of companies experienced disruptions to network security business practices due to the sudden shift to a work from home model, and 78% of corporate VPNs have experienced some connectivity issues. The VIAVI State of the Network Study of IT professionals found that VPN oversubscription was one of the top challenges of managing remote user traffic growth, with remote end-user experience being the highest ranked requirement for operational visibility. Issues such as the inability to access VPN at peak times, poor conference call quality, and slow application response times have caused significant challenges.